請問產生真隨隨機數是不是需要一個物理信號?這個信號怎麼獲得呢?
在調用 tls_crypto_trng() 函數時,在開始階段,是不是需要收到物理信號才會產生隨機數?那麼這端程序邏輯是什麼流程呢?如何搭配物理設備可以收到這個信號?現在有溫濕度傳感器,陀螺儀,氣壓傳感器。
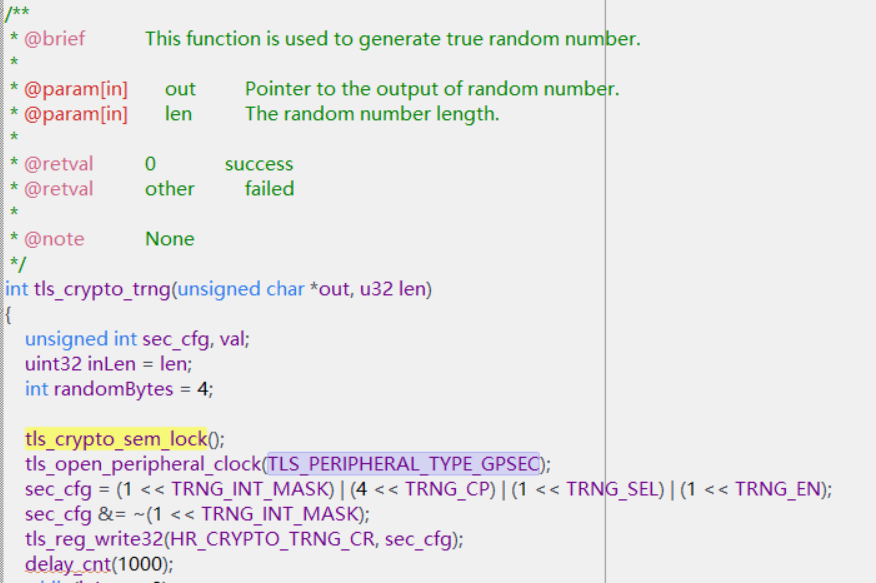
在調用 tls_crypto_trng() 函數時,在開始階段,是不是需要收到物理信號才會產生隨機數?那麼這端程序邏輯是什麼流程呢?如何搭配物理設備可以收到這個信號?現在有溫濕度傳感器,陀螺儀,氣壓傳感器。



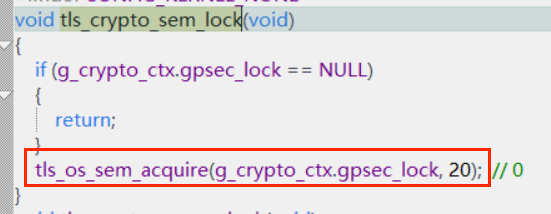
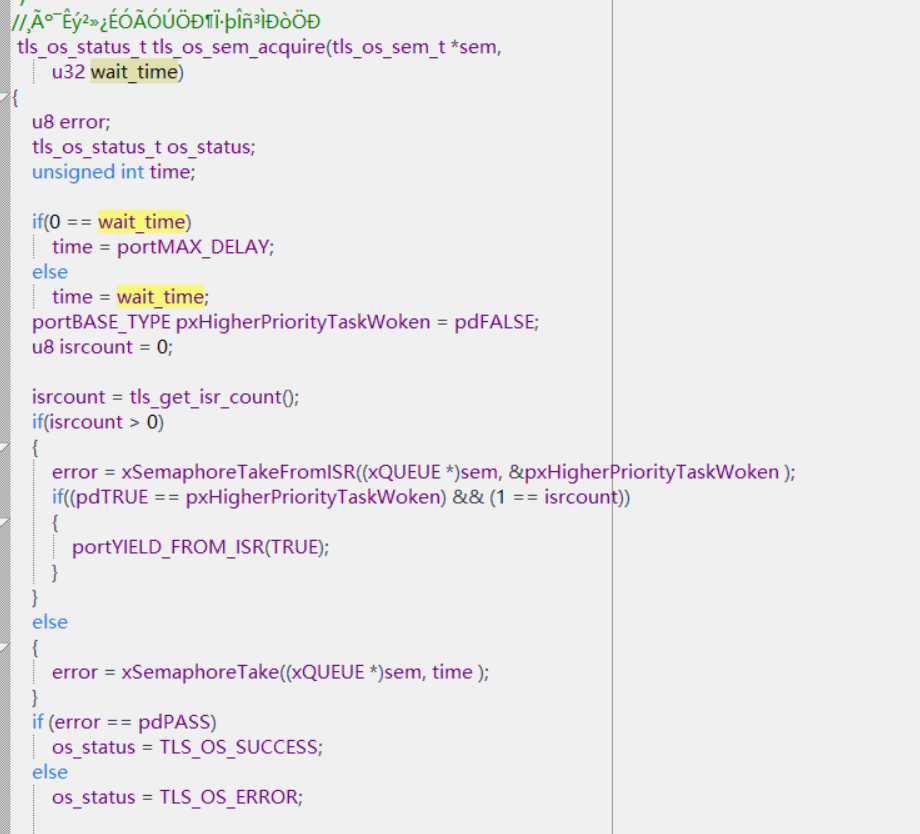
g_crypto_ctx.gpsec_lock定義的是一個互斥鎖,在SDK的初始化時有調用tls_crypto_init,在這裡創建了該信號量,初始值是1,所以在沒有其他地方用到該模塊時,調用tls_os_sem_acquire(g_crypto_ctx.gpsec_lock, 0);會立即返回接著往下執行。如果有其他地方調用了就會等待,直到能獲取到信號量才能接著往下執行,起到一個互斥鎖的功能。調用tls_os_sem_acquire獲取,信號量的個數會減一,調用tls_os_sem_release釋放,信號量的個數會加一,這兩個接口是成對使用的。在使用信號量實現互斥鎖的功能時,創建信號量時初始值會設置為1,這樣有一個地方獲取了鎖的使用權後,其他地方就需要等待這裡釋放了才能獲取,起到防止出現同一個模塊或者變量或者接口被同時操作的情況。並不是一個物理信號。
Hello! SDK for w80x is still at the conceptual stage in our team.
We have not yet thoroughly understood how this pie works :)) For HAL 0.6.0, extracting true random numbers was easy. You can see this technique in our Arduino core. Methods trng_init() and rng_Get(). There is no need for a special signal to generate a random number. A noise-like signal is generated on the cryptomodule crystal. There is a description of this in the datasheet.
Thank you very much for your reply! I am developing with the SDK as shown in the figure below. I don't know where the Arduino core you mentioned is, as there is no relevant explanation in the materials provided by the manufacturer. Could you explain it in more detail? Also, I found that when the wait time is set to 0, it seems to be waiting for a signal all the time, so no true random number is generated. So when the wait time is set to 20, is it generating pseudo-random numbers?
@1201 Sorry, but I don't understand what your problem is.
Let's look at random number generation as programmers who are not familiar with the internal structure of the w80x chip. What do we usually do? We use two functions from stdlib - srand(time(NULL)) and rand(). This way we get a non-repeating pseudo-random sequence. Exploring the SDK-W80X we will find the definitions and prototypes we need for generation in the files wm_crypto_hard.h and *.c
It says that by default the generation of a true random number works -
define USE_TRNG 1
By analogy with stdlib, we need to initialize the generator using the function
int tls_crypto_random_init(u32 seed, CRYPTO_RNG_SWITCH rng_switch);
In this case, the seed parameter will not affect the sequence, because the white noise generator is running.
The next step is to get a pointer to a random number using the function int tls_crypto_trng(unsigned char *out, u32 len);
And that's enough.
I have another question - Why do they slow down the core by calling the function delay_cnt(1000);? White noise turns on during initialization and runs until we stop it.
@1201 To expand on my answer... The semaphore blocking may be due to the fact that this is a critical section according to the SDK developers. If you don't have a deep understanding of how RTOS works, you don't need to go there. :)
@AnatolSher I know that if random numbers generated with a seed are pseudo-random, then I have a question: is it certain that the tls_crypto_trng() function can generate true random numbers? Looking forward to your response. Thank you.
@1201 Be confident. Datasheets usually don’t write nonsense :)
See section 7.3.8 on page 63.
The difference between a true random number generator (TRNG) and a pseudo random number generator (PRNG) is that an TRNG uses unpredictable physical means to generate numbers (such as junction noise), while a PRNG uses mathematical algorithms (entirely computer generated).
@1201 junction noise = semiconductor P-N junction noise
This is not a predictable phenomenon
@AnatolSher Where can I find datasheets?
@1201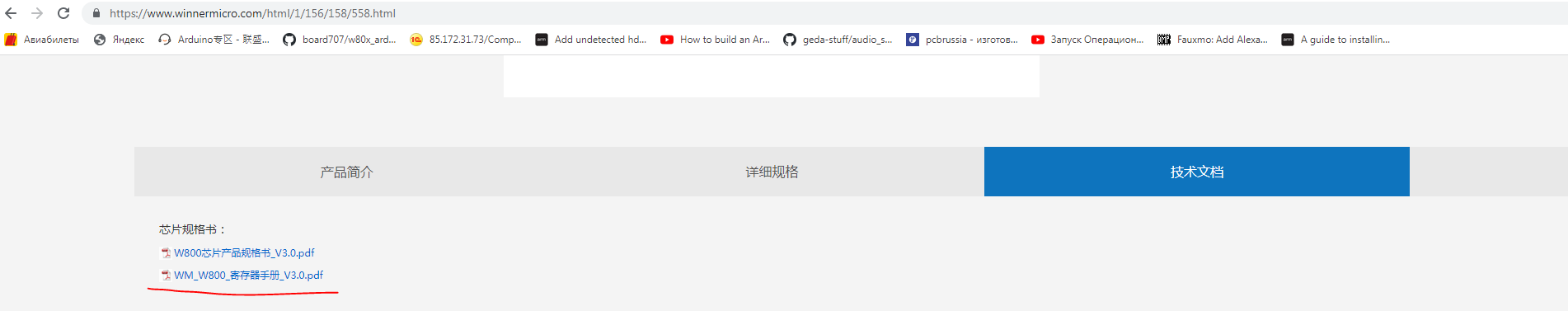
https://www.winnermicro.com/html/1/156/158/558.html
@1201 http://ask.winnermicro.com/article/3.html
@AnatolSher I have read this document but I did not find what I was looking for.0.0